IT Security Incident Response Policy
Approved by the API-Enfance Board of Directors on December 18, 2023.
Purpose
This policy defines the requirements for reporting and responding to incidents related to the Organization’s information systems and operations. This policy applies to all Employees and Partners of the Organization, including, but not limited to, its business units and subsidiaries.
Definitions
1) Organization
API-Enfance, a non-profit legal person incorporated under Part 3 of the Companies Act (RLRQ, c. C-38), having its head office at 1024, rue de Nouë, Quebec City (Québec) G1W 4L3, registered in the Registraire des entreprises du Québec under number 1175257550.
Coordonnées :
+1 (819) 200-0203
info@api-enfance.ca
2) Employee
Any person bound to the Organization by a contract of employment, in accordance with the regulations in force.
3) Partner
Any person not employed by API-Enfance who is contractually bound to collaborate with the Organization.
4) Website
Refers to the website created and developed by the Organization, accessed through the https://api-enfance.ca domain, and redirecting users to the Web Application.
5) Web Application
Refers to the application software hosted on a server and accessed via a web browser created and developed by the Organization and supporting the Blooming Words™ program, including the improvements. The use of the Web Application does not require installation on any physical computer hardware.
The Web Application includes the following elements:
– https://app.api-enfance.ca domain and all related applications,
– User Management Module (Dashboard),
– Training Modules,
– Technical Support Module.
6) Password
An arbitrary string of characters chosen by a User, used to authenticate him when he attempts to log in, in order to prevent unauthorized access to his account.
7) IT Manager
An employee or partner responsible for managing the Organization’s multi-user computing environment. The IT department manager is usually responsible for installing and configuring system hardware and software, creating and managing User accounts, upgrading software, as well as backup and recovery tasks.
8) User
Means any person required to use the Web Application, or any person browsing the Site.
9) Legal Advisor
A person identified by senior management as the point of contact for legal matters.
10) Executive Management
Includes Executive Director and Deputy Director(s).
11) Designated Persons and Designated Channels
If you have any questions, or if you have an incident, please contact privacy@api-enfance.ca. It is also possible to write to the Organization by post at the above address.
Policy
1) Preface
This policy includes roles, responsibilities and communication strategies in the event of a compromise, including notification of relevant external partners.
Specific areas addressed in the policy include:
– Incident response procedure,
– Resolution and business continuity,
– Data backup process,
– Analysis of legal incident reporting requirements,
– Identification and protection of all critical system components,
– Reference to incident response procedures of relevant partners.
2) IT Security Response Team
Creation of the Response Team
The Organization’s Executive Management must organize and maintain a Computer Security Response Team, or be in contact with a third-party security response service provider, capable of providing expedited problem notification, damage control and problem correction services in the event of computer-related emergencies, such as virus infestations and hacker intrusions.
Response Team Responsibilities
The IT Security Response Team must develop, periodically update and regularly test emergency response plans that provide for the continued operation of critical IT and communications systems in the event of service interruption or degradation.
Response Team Availability
The Organization’s IT Security Response Team must always be available to respond to alerts including, but not limited to, evidence of unauthorized activity, detection of unauthorized wireless access points, critical intrusion detection alerts and reports of unauthorized modifications to critical systems or content files.
3) Roles and Responsibilities
Incident Management
The members of the IT Security Response Team must be clearly defined by Executive Management. These individuals must be given the authority to define the procedures and methodologies that will be used to manage specific security incidents.
Designated Person for All Security Events
Unless they are expressly recognized as authorized spokespersons for the Organization, no Employee may speak to the press or any other external party about the current status of an emergency situation or a recently experienced security incident.
Information for Legal Proceedings
Employees or Partners are prohibited from providing Agency records, or copies thereof, to outside third parties or government officials, whether in response to a subpoena or otherwise, unless they have obtained prior authorization from the Organization’s Executive Management. Similarly, Employees are prohibited from testifying about facts that come to their knowledge in the course of their official duties, unless they have obtained prior authorization from the Organization’s Executive Management.
Password Management and Two-factor Authentication
To prevent unintentional disclosure of sensitive information, Employees and Partners of the Organization must use a password manager approved by the IT Manager. Passwords must contain a minimum of 11 alphanumeric characters and include at least one special character.
In addition, the Organization’s Employees and Partners must activate and use, where possible, a two-factor authentication (2FA) system on all software, applications, the web application or any other system or software enabling access to Users’ personal data. 2FA is also required for the Organization.
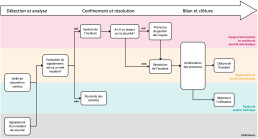
4) Incident Response
Intrusion Response
The IT department manager must document and periodically review intrusion response procedures. These procedures should include the sequence of actions that the Organization’s Employees and Partners should follow in the event of a suspected intrusion into the information system, who has the authority to perform which actions in response, and what resources are available to assist in the response. All Employees and Partners required to follow these procedures must be periodically trained and familiarized with them.
Resolution of Information Security Incidents
All information security incidents must be handled with the participation and cooperation of the IT Security Response Team.
Security Modifications After System Compromise
Whenever a system has been compromised, or is suspected of having been compromised by an unauthorized party, the IT Manager must immediately have a reliable version of the operating system and all security-related software reloaded, and all recent changes to permissions and access must be examined for possible unauthorized modifications.
Suspected System Intrusions
Whenever a system is suspected of having been compromised, the computer concerned must be immediately disconnected from all networks, and predetermined procedures must be followed to ensure that the system is free from compromise before it is reconnected to the network.
Unauthorized Access Problems
Whenever unauthorized access to the system is suspected or proven, the Organization’s Employees or Partners must take immediate action to stop such access, or request assistance from the IT Manager.
Confidentiality of Internal Investigations
Until charges are laid or disciplinary action taken, all investigations into allegations of criminal or abusive behavior must be kept strictly confidential in order to preserve the reputation of the suspected party.
Participation in Legal Proceedings
Any Employee or Partner of the Organization summoned by subpoena or otherwise before a judicial board or government agency, in connection with services provided by the Organization, must immediately notify the Organization’s Legal Counsel and Executive Management in writing.
5) Monitoring and Recording the Use of Shared Resources
The use of all the Organization’s shared IT resources used for production activities must be continuously monitored and recorded. This usage history data must then be provided in real time to security alert systems designated by the IT Manager (intrusion detection systems, virus detection systems, spam detection systems, etc.).
6) Reporting Incidents
Incident Report
All suspected information security incidents should be reported as quickly as possible via the Organization’s designated Communication Channel.
Information Security Alert Systemn
The IT Manager shall establish, maintain and periodically test a communication system enabling the Organization’s Employees and Partners to promptly report any suspected information security problems to the appropriate staff members.
Reporting Alternatives
The Organization’s Employees may also immediately report all suspected information security issues, vulnerabilities and incidents to their line manager.
Whistleblower Protection
The Organization will protect Employees who report in good faith what they believe to be violations of laws or regulations, or conditions that may endanger the health or safety of other Employees. This means that such Employees will not be dismissed, threatened or discriminated against because they report what they consider to be wrongdoing or a dangerous situation.
Employees who report a security problem, vulnerability or situation contrary to the Organization’s Code of Ethics to the IT Manager may, at their sole discretion, have their identity kept strictly confidential. This means that the whistle-blower’s identity will not be revealed to his or her line manager, to other members of General Management, or to other employees of the Organization who are not directly involved in the receipt of the report.
7) Events to Report
Damage and Loss of Off-site Systems
Employees must report immediately to their line manager and to the IT Manager any damage or loss of hardware, software or Organization’s information entrusted to them.
System Alerts and Warnings
Employees and Partners must promptly report all security alerts, warnings, suspected vulnerabilities and the like to the Technical Support Department. Employees and Partners are prohibited from using the Organization’s systems to transmit such information to others, whether internal or external to the Organization.
Unauthorized Activities
Employees and Partners must immediately report any unauthorized loss or modification of computerized production data to the IT Manager. Any suspicious use of files, databases or communication networks must also be reported immediately to the IT Manager.
Unexpected Requests for Login Information
Apart from the regular and expected login screens, Users should be wary of all pop-ups, websites, instant messages and other requests for API-Enfance usernames and passwords. Users who encounter such requests should refrain from providing their API-Enfance username and password, and promptly report the circumstances to Technical Support.
Unintentional Disclosure of Sensitive Information
Unintentional disclosure of the Organization’s sensitive information is a serious matter and must be reported immediately to both the Executive Management and the Security Committee of the Organization’s Board of Directors. Such reporting must take place as soon as the disclosure is known, or as soon as there are reasonable grounds to believe that a disclosure has taken place.
Software Malfunctions
All apparent software malfunctions must be reported immediately to Executive Management or IT Manager.
Unauthorized Wireless Access Points
If an unauthorized wireless access point is detected on the API-Enfance network, the IT Security Response Team must be informed.
8) Reporting to Third Parties
External Breach Report
Unless required by law or regulation to report information security breaches to external authorities, Executive Management, in collaboration with Legal Counsel (or his or her designee) and the IT Security Response Team must evaluate the advantages and disadvantages of external disclosure before reporting such breaches.
Reporting Suspected Security Breaches to Third Parties
If a verifiable information systems security problem, or a suspected but probable problem, has resulted in the exposure of third-party private or confidential information to unauthorized persons, these third parties must be informed of the situation immediately (within three calendar days). Appendix D provides a sample letter that can be used to communicate.
Loss or Disclosure of Sensitive Information
If sensitive information is lost or disclosed to unauthorized parties, or if it is suspected that it has been lost or disclosed to unauthorized parties, the owner of the information and the IT Manager must be informed immediately (within three calendar days).
Exploitation of System Vulnerabilities and Victim Information
Organization’s Employees and Partners must not publicly disclose information about individuals, organizations or specific systems that have been damaged by computer crime and abuse. Similarly, the specific methods used to exploit certain system vulnerabilities must not be publicly disclosed.
Disclosure of Supplier Vulnerabilities
If the Organization’s Employees or Partners discover a serious vulnerability in an information system, and that vulnerability can be directly attributed to a weakness in the hardware and/or software of a certain supplier, that supplier must be promptly and confidentially informed of the problem by the IT Manager.
9) Contacting the Authorities
Contacts with Law Enforcement Agencies and the Criminal Justice System
Every decision concerning the involvement of law enforcement agencies in information security incidents or problems must be taken by the Organization’s Executive Management. Similarly, any contact informing law enforcement agencies of an information security incident or problem must be initiated by the IT Manager.
Thus, the IT Manager and his staff must not contact the police or other members of the justice system about information systems problems, unless they have received written authorization from the Organization’s Executive Management.
Cooperation Request in Investigations
The Organization’s Employees and Partners must immediately report any request to participate in an information security investigation to Legal Counsel. Any form of cooperation with the requester is prohibited until Legal Counsel determines that participation is lawful, unlikely to cause problems for the Organization and requested by an authorized party.
Thus, even if the requester claims to be a member of law enforcement, the Organization’s Employees and Partners must not disclose any of the Organization’s internal information through any communication mechanism, unless Legal Counsel has established the authenticity of the person’s identity and the legitimacy of the request.
10) Handling Data Breaches
Data Breach Response Procedure
The Organization’s Executive Management in collaboration with the IT Security Response Team shall prepare, test and annually update a Data Breach Response Procedure that addresses cases of breach of Users’ sensitive data.
11) Incident Review
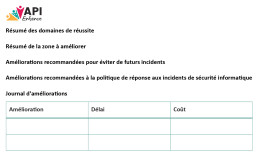
Continuous Improvement of IT Security Incident Response Procedure
The IT security incident response procedure must be updated to reflect lessons learned from actual incidents.
The IT security incident response procedure must also be updated to reflect industry developments.
Incident Records
The IT Manager is responsible for establishing and maintaining an incident logging process to record all incidents experienced by the Organization.
Incident Feedback
The IT Manager must prepare an annual retro-analysis of reported information security incidents and data breaches.
12) Gathering Evidence
Evidence of Computer Crime or Abuse
To provide evidence for investigation, prosecution and disciplinary action, certain information must be collected immediately when computer crime or abuse is suspected. Information to be collected immediately includes the current system configuration as well as backup copies of all files potentially involved.
Evidence Storage
Information relevant to the IT investigation should then be stored securely offline by the IT Manager until it is handed over to another authorized person, or until Legal Counsel determines that the Organization will no longer need the information.
Sources of Digital Evidence
For each production IT system, the IT Manager must identify sources of digital evidence that could reasonably be used in a court case. These sources of evidence must then be subject to a standardized collection, retention and destruction process comparable to that used for essential documents.
Responsibility for the Production of Digital Evidence
The Organization’s Executive Management delegates to the IT Manager the responsibility for coordinating the discovery and presentation of digital evidence that may be required to support litigation.
Classification of Evidence
Agency data that may be considered electronic evidence shall be classified as CONFIDENTIAL and shall only be accessed by authorized representatives of the IT Security Response Team or approved third parties involved in the investigation.
13) Criminal Investigation
IT Crime Investigation
Whenever the evidence clearly shows that the Organization has been the victim of a IT or communications crime, a thorough investigation must be carried out. This investigation must provide sufficient information for the Executive Management to take action to ensure that (1) such incidents do not recur in the future, and (2) effective security measures have been re-established.
Forensic Analysis Process
Any analysis or investigation using data storage media containing information that could at some point become important evidence in a trial for computer crime or computer abuse must be carried out using a copy rather than the original version. This will help prevent any unforeseen changes to the original information.
Investigation Status Reports
The status of information security investigations is to be reported to the Organization only by the lead investigator or management representative of the investigation team.
Information on IT Crime Investigations
All evidence, ideas and hypotheses concerning IT crimes suffered by the Organization, including possible methods of attack and the intentions of the perpetrators, must be communicated to Legal Counsel and considered restricted and confidential information protected by law.
Information Security Investigations
All internal Organization investigations of information security incidents, violations and problems shall be conducted by the IT Manager.
Information Security Investigation Team
Any person who knows the suspects personally, or who maintains friendly relations with them, for reasons of conflict of interest, is excluded from participation in an information security incident investigation team.
Details of Incident Investigations
Details of ongoing information systems incident investigations must not be sent by e-mail. Similarly, to prevent such information falling into the hands of intruders, files describing an investigation in progress should not be stored on potentially compromised systems, or anywhere on an associated network where they could reasonably be accessed by intruders.
14) Violations
Any violation of this policy may result in disciplinary action, including dismissal. The Organization reserves the right to report any illegal activity to the appropriate authorities and to cooperate in any investigation of such activity. The Organization does not consider conduct in violation of this policy to be a normal part of an Employee’s or Partner’s business, or a direct consequence of the performance of their duties. Accordingly, to the extent permitted by law, the Organization reserves the right not to defend or pay damages awarded to Employees or Partners resulting from a violation of this policy.